I'm Going Phishing
OK, OK, so this is not the sort of fishing that will put dinner on the table for you and your family. However, the advice in the video below may help you avoid the criminals phishing for your personal information. Sometimes the trap is so well hidden that even the most experienced can be fooled into clicking a dubious link. Watch the video for more info.
I am the 'Geek Ambassador' for Hotspot Shield ...
Get behind the Shield here http://bit.ly/hshield
Feds tell Web firms to turn over user account passwords

The U.S. government has demanded that major Internet companies divulge users' stored passwords, according to two industry sources familiar with these orders, which represent an escalation in surveillance techniques that has not previously been disclosed.
If the government is able to determine a person's password, which is typically stored in encrypted form, the credential could be used to log in to an account to peruse confidential correspondence or even impersonate the user. Obtaining it also would aid in deciphering encrypted devices in situations where passwords are reused.
"I've certainly seen them ask for passwords," said one Internet industry source who spoke on condition of anonymity. "We push back."
A second person who has worked at a large Silicon Valley company confirmed that it received legal requests from the federal government for stored passwords. Companies "really heavily scrutinize" these requests, the person said. "There's a lot of 'over my dead body.'"
Some of the government orders demand not only a user's password but also the encryption algorithm and the so-called salt, according to a person familiar with the requests. A salt is a random string of letters or numbers used to make it more difficult to reverse the encryption process and determine the original password. Other orders demand the secret question codes often associated with user accounts...
Read the full story here. Source: CNET
Government Officials Bring in Security Experts to Test iOS 7's Activation Lock Feature
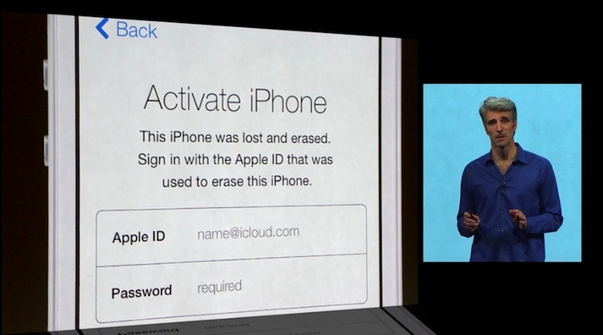
After launching an investigation into the anti-theft practices of smartphone manufacturers like Apple, New York Attorney General Eric Schneiderman and San Francisco District Attorney George Gascón will today test how Apple’s Activation Lock feature holds up against determined thieves, reports CNET.
First introduced at WWDC, Activation Lock is designed to prevent Find My iPhone from being deactivated, which keeps stolen iPhones from being wiped and reactivated. The feature is included in iOS 7, which is expected to be released to consumers this fall.
Gascón and Schneiderman are planning to bring in security experts from the Northern California Regional Intelligence Center to attempt to bypass Activation Lock in order to gain access to an iPhone. The security team will also test the Lojack for Android software on a Samsung Galaxy S4.
"While we are appreciative of the efforts made by Apple and Samsung to improve security of the devices they sell, we are not going to take them at their word," Schneiderman and Gascón said in a joint statement. "Today we will assess the solutions they are proposing and see if they stand up to the tactics commonly employed by thieves."
The two officials have pushed for greater anti-theft measures from cell phone manufacturers after a spike in mobile device thefts. While carriers agreed last year to develop a centralized database to track stolen phones, it has proven to be largely ineffectual. Both Gascón and Schneiderman have stated that they believe Activation Lock is an inadequate theft deterrent and Gascón has urged Apple to implement a "kill switch" that would permanently disable stolen iOS devices.
The results of the Activation Lock investigation are expected to be released later today.
Source: Mac Rumours
Facebook Android app security flaw affects those who don’t even use the app

While it’s not clear just why the app would do this, or what purpose it has for doing so, the Facebook app for Android is taking your phone number the first time you open it up. Without even logging in, the app takes your number and stores it on the Facebook servers. You don’t need a Facebook account, or even initiate an action within the app. Simply having it and opening it will allow the app to take your phone number.
Norton discovered this security flaw during routine testing they perform on apps for their Mobile Insight security app. According to Norton, their testing methods are sound:
Through automatic and proprietary static and dynamic analysis techniques, Mobile Insight is able to automatically discover malicious applications, privacy risks, and potentially intrusive behavior. Further, Mobile Insight will tell you exactly what risky behavior an application will perform and give you specific, relevant, and actionable information.
-norton
Norton then reached out to Facebook, who claimed to be unaware of the issue. They told Norton they“did not use or process the phone numbers and have deleted them from their servers”, and said they had no knowledge of the issue. Norton also notes that Facebook is not the only app doing this, or even the worst offender. They promise more information on other culprits in coming weeks, but we’re still curious why Facebook would take numbers from a device that wasn’t even logged in. If I were to download the app, then open it to see what it looked like out of curiosity, my number would then be uploaded to the Facebook server.
We’re not ready to call Facebook nefarious on this account. Giving them the benefit of the doubt, even in the face of all their other security flaws, we’ll chalk this up to another error on their part. What this does do is bring into focus app permissions, and how important they are. Perhaps more importantly, how they can be abused by the app publisher, and ignored by users as fine-print.
Source: Android Authority
Two-step verification starts rolling out for Microsoft accounts
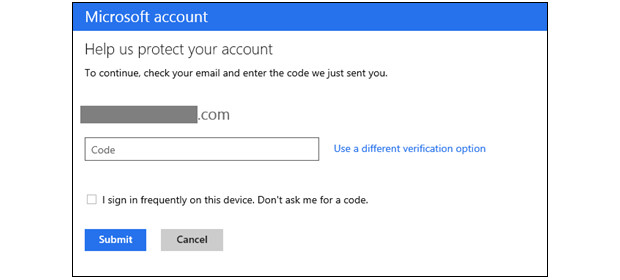 Everyone else is doing it, so why not Microsoft, right? The company has been accused of playing the "me too" game in the past, but we're not going to complain when the the end result is better security. As we learned from a leak last week, Redmond will begin enabling two-step verification for Microsoft accounts. The switch will get flipped for everyone over the next few days and, with email, Xbox Live and Skype (just to name a few) associated with the service formerly known as Live, it's never been more important to keep it locked down. (Especially when others are learning this lesson the hard way.) The two-factor gateway is purely opt-in, except where it's already been required: editing credit card information and accessing SkyDrive from a new computer. There's even a dedicated authenticator app for Windows Phone 8, which works whether or not you've got an internet connection. There's loads more detail at the source and you can check to see if the feature has been turned on for your account at the more coverage link. And if you can, we strongly suggest you turn it on. Like, now.
Everyone else is doing it, so why not Microsoft, right? The company has been accused of playing the "me too" game in the past, but we're not going to complain when the the end result is better security. As we learned from a leak last week, Redmond will begin enabling two-step verification for Microsoft accounts. The switch will get flipped for everyone over the next few days and, with email, Xbox Live and Skype (just to name a few) associated with the service formerly known as Live, it's never been more important to keep it locked down. (Especially when others are learning this lesson the hard way.) The two-factor gateway is purely opt-in, except where it's already been required: editing credit card information and accessing SkyDrive from a new computer. There's even a dedicated authenticator app for Windows Phone 8, which works whether or not you've got an internet connection. There's loads more detail at the source and you can check to see if the feature has been turned on for your account at the more coverage link. And if you can, we strongly suggest you turn it on. Like, now.
[Source: Engadget]
Apple is Aware of Apple ID Exploit, is Working on a Fix
 Soon after word hit about the unbelievably easy Apple ID exploit, Apple has responded by saying it’s already working on a fix. As it should be. If it’s not happening on the mobile side, issues are springing up elsewhere.
Soon after word hit about the unbelievably easy Apple ID exploit, Apple has responded by saying it’s already working on a fix. As it should be. If it’s not happening on the mobile side, issues are springing up elsewhere.
In a statement to The Verge, the company lamented the glaring issue and said it takescustomer privacy very seriously. Let’s hope Apple can tie this one up quick, too. All someone needs to take control of someone else’s Apple ID is their email and date of birth—you can get that kind of information on Facebook very easily.
As of now, Apple has taken down its iForgot password reset tool as a temporary solution. That might be an acceptable short-term fix, but in the long run, let’s hope Apple develops a stricter protocol when reseting a password. Apple IDs are the key to Apple’s content kingdom; if user IDs start running rampant, who knows what kind of backlash the company will face.
[Source: TechnoBuffalo]
Apple adds two-factor authentication to your Apple ID
 Apple is beefing up the security of its Apple ID by adding two-factor authentication to the account login process. Customers concerned about unauthorized access to their Apple ID can login to their account at Apple'sMy Apple ID webpage and turn on the feature as described below
Apple is beefing up the security of its Apple ID by adding two-factor authentication to the account login process. Customers concerned about unauthorized access to their Apple ID can login to their account at Apple'sMy Apple ID webpage and turn on the feature as described below
- Go to My Apple ID (appleid.apple.com)
- Click the "Manage your Apple ID" button to login to your Apple ID
- Enter your Apple ID and password and click "Sign In"
- Select "Password and Security" in the left-hand column
- Type in the answers to your account security questions if you are prompted to answer them.
- You will see Two-Step Verification at the top of the page. Click on "Get Started" and follow the on-screen instructions.
If you have two-factor verification enabled, you will be required to enter both your password and a 4-digit code to verify your identity. According to Apple's support page, you will need this information whenever you sign in to My Apple ID to manage your account, make an iTunes / App Store / iBookstore purchase from a new device or get Apple ID-related support from Apple. You can read more about the security feature on Apple's support website, and check out Glenn Fleishman's thorough pros and cons rundown on TidBITS.
[Source: TUAW]
Hacker sentenced to 41 months for exploiting AT&T iPad security flaw
 Hacker Andrew "Weev" Auernheimer was found guilty last year of spoofing iPad user IDs to gain access to an AT&T email database, and he's now been sentenced to 41 months in prison. The time was chalked up to one count of identity fraud and one count of conspiracy to access a computer without authorization. In addition to the nearly three and a half years behind bars, Auernheimer also faces another three years of supervised release, and restitution payments of $73,000 to AT&T.
Hacker Andrew "Weev" Auernheimer was found guilty last year of spoofing iPad user IDs to gain access to an AT&T email database, and he's now been sentenced to 41 months in prison. The time was chalked up to one count of identity fraud and one count of conspiracy to access a computer without authorization. In addition to the nearly three and a half years behind bars, Auernheimer also faces another three years of supervised release, and restitution payments of $73,000 to AT&T.
Prosecutors in the case were asking for a four-year sentence, and reports say that they used both a Reddit Ask Me Anything post that Auernheimer did as well as quotes from the Encyclopedia Dramatica wiki. Auernheimer did give a statement before the sentencing, where he both read out a John Keats poem, and said that he was "going to jail for doing arithmetic."
Auernheimer has promised that he will appeal the sentencing, so this may not be the last we've heard of "Weev" just yet.
[Source: TUAW]
Evernote plans two-factor authentication following last week's hack
 In a move that's often more reactive than proactive these days, Evernote has shared plans to add two-factor authentication to its login process. This latest announcement follows last week's hacking attack and subsequent site-wide password reset, and will be available to all of the site's 50 million users beginning later this year, according to an InformationWeek report. It's too early to say exactly how the Evernote team plans to implement the new security feature, whether through a dedicated app or text message password, but given the service's scale, we can likely count out a hardware fob option, at least. For now, your best course of action is to create a secure password, or, if you're especially paranoid, you may consider delaying your return until the security boost is in place.
In a move that's often more reactive than proactive these days, Evernote has shared plans to add two-factor authentication to its login process. This latest announcement follows last week's hacking attack and subsequent site-wide password reset, and will be available to all of the site's 50 million users beginning later this year, according to an InformationWeek report. It's too early to say exactly how the Evernote team plans to implement the new security feature, whether through a dedicated app or text message password, but given the service's scale, we can likely count out a hardware fob option, at least. For now, your best course of action is to create a secure password, or, if you're especially paranoid, you may consider delaying your return until the security boost is in place.
[Source: Engadget]
Evernote forcing users to change password after hacking attempt
 Evernote, the popular cross-platform note taking and sharing app, has issued a statement about some recent "suspicious activity on the Evernote network". All users will have to change their password, and it seems that user names, and other data that includes the encrypted version of passwords has been accessed. In a letter sent out to users, Evernote says the following:
Evernote, the popular cross-platform note taking and sharing app, has issued a statement about some recent "suspicious activity on the Evernote network". All users will have to change their password, and it seems that user names, and other data that includes the encrypted version of passwords has been accessed. In a letter sent out to users, Evernote says the following:
The investigation has shown, however, that the individual(s) responsible were able to gain access to Evernote user information, which includes usernames, email addresses associated with Evernote accounts, and encrypted passwords. Even though this information was accessed, the passwords stored by Evernote are protected by one-way encryption. (In technical terms, they are hashed and salted.)
While our password encryption measures are robust, we are taking steps to ensure your personal data remains secure. This means that in an abundance of caution, we are requiring all users to reset their Evernote account passwords. Please create a new password by signing into your account on evernote.com.
After signing in, you will be prompted to enter your new password. Once you have reset your password on evernote.com, you will need to enter this new password in other Evernote apps that you use. We are also releasing updates to several of our apps to make the password change process easier, so please check for updates over the next several hours.
As we've seen recently, there's a rash of coordinated attempts to hack the big players in online services. Hopefully Evernote's encryption methods are solid, but having users change their password at log in is a great way to keep everyone safe. Visit Evernote's blog for more information.
[Source: AndroidCentral]
Yet another Java vulnerability discovered, researchers recommend disabling browser plug-in
 Following an attack on a smaller number of corporate Macs that exploited exploited a flaw in the Java browser plug-in, researchers from security firm FireEye are warning users of yet another new Java zero-day vulnerability. According to a blog post published yesterday (via IDG), browsers running Java v1.6 Update 41 and Java v1.7 Update 15 are currently vulnerable to a malware attack that installs a remote access tool known as McRAT. The exploit is reportedly different from the one used to attack Facebook, Twitter, Apple and several other companies last month. Following the earlier attack, Apple released an updateto Java for users to version 1.6.0_41. These recent vulnerabilities come after several updates over the past year to Java addressing exploits.
Following an attack on a smaller number of corporate Macs that exploited exploited a flaw in the Java browser plug-in, researchers from security firm FireEye are warning users of yet another new Java zero-day vulnerability. According to a blog post published yesterday (via IDG), browsers running Java v1.6 Update 41 and Java v1.7 Update 15 are currently vulnerable to a malware attack that installs a remote access tool known as McRAT. The exploit is reportedly different from the one used to attack Facebook, Twitter, Apple and several other companies last month. Following the earlier attack, Apple released an updateto Java for users to version 1.6.0_41. These recent vulnerabilities come after several updates over the past year to Java addressing exploits.
FireEye is recommending users disable Java until Oracle addresses the issue:
We have notified Oracle and will continue to work with Oracle on this in-the-wild discovery. Since this exploit affects the latest Java 6u41 and Java 7u15 versions, we urge users to disable Java in your browser until a patch has been released; alternatively, set your Java security settings to “High” and do not execute any unknown Java applets outside of your organization.
Oracle provides the instructions below for uninstalling Java on Mac:
- Click on the Finder icon located in your dock
- Click on Applications tab on the sidebar
- In the Search box enter JavaAppletPlugin.plugin
- This will find the JavaAppletPlugin.plugin file
- Right click on JavaAppletPlugin.plugin and select Move to Trash
[Source: 9to5Mac]
